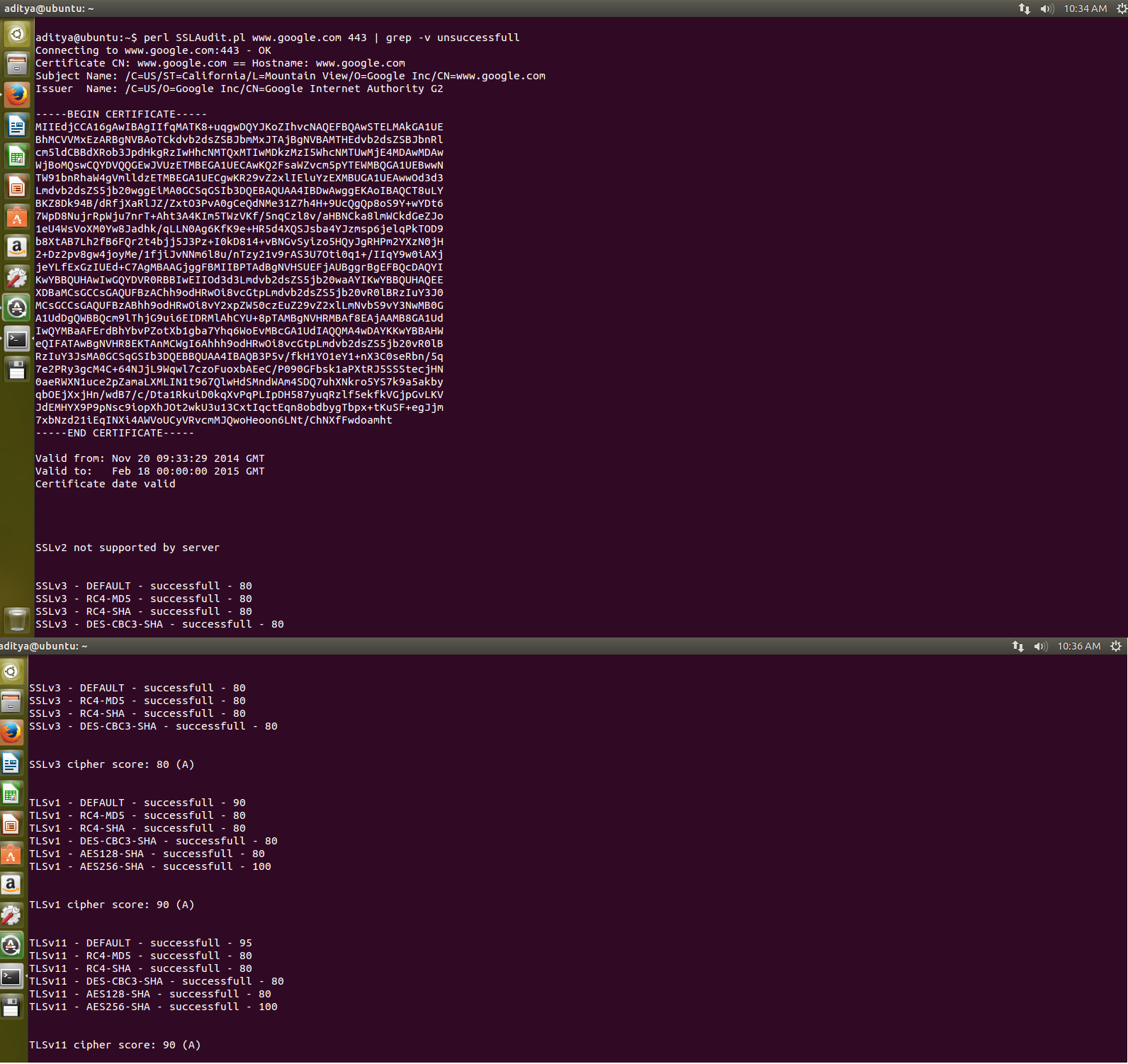
Just performs a handshake with the list of JSSE ciphers with the SSL server. If handshake is successful it marks it as a success. This is more of a test for Java based SSL clients which use JSSE for SSL/TLS communication. This code relies heavily on the underlying implementation provided by Java JDK/JSSE. Use it with 1.7 as a lot of cipher support has been added. As I mentioned, this is not a true SSL cipher scanner, because it depends on what ciphersuites have been enabled by JSSE. The server might support other ciphers that are not yet implemented by JSSE, but they wont turn up in the results. Actually if you can read from the raw SSL handshake packets, you can understand what the server SSL supports, you do not need java implementation for that.
package com.ssl.test;
import java.util.ArrayList;
import java.util.Collections;
import javax.net.ssl.SSLSocket;
import javax.net.ssl.SSLSocketFactory;
public class SSLTesting {
private static final int PORT_TARGET = 443;
private static final String HOST = "www.example.com";
private static final String PROTO_SSLV3 = "SSLv3";
private static final String PROTO_TLSV1 = "TLSv1";
private static final String PROTO_TLSV11 = "TLSv1.1";
private static final String PROTO_TLSV12 = "TLSv1.2";
private static final boolean VERBOSE = false;
// Note 1: Standard names for all the cipher suites, not all are yet implemented
// http://docs.oracle.com/javase/7/docs/technotes/guides/security/StandardNames.html#ciphersuites
// Note 2: All the ones supported by Java 7
// http://docs.oracle.com/javase/7/docs/technotes/guides/security/SunProviders.html#SunJSSEProvider
//See Note 2.
private static final String jsseCiphersDisabledByDefault = "TLS_DH_anon_WITH_AES_256_CBC_SHA256:TLS_ECDH_anon_WITH_AES_256_CBC_SHA:TLS_DH_anon_WITH_AES_256_CBC_SHA:"
+ "TLS_DH_anon_WITH_AES_128_CBC_SHA256:TLS_ECDH_anon_WITH_AES_128_CBC_SHA:TLS_DH_anon_WITH_AES_128_CBC_SHA:TLS_ECDH_anon_WITH_RC4_128_SHA:"
+ "SSL_DH_anon_WITH_RC4_128_MD5:TLS_ECDH_anon_WITH_3DES_EDE_CBC_SHA:SSL_DH_anon_WITH_3DES_EDE_CBC_SHA:TLS_RSA_WITH_NULL_SHA256:"
+ "TLS_ECDHE_ECDSA_WITH_NULL_SHA:TLS_ECDHE_RSA_WITH_NULL_SHA:SSL_RSA_WITH_NULL_SHA:TLS_ECDH_ECDSA_WITH_NULL_SHA:TLS_ECDH_RSA_WITH_NULL_SHA:"
+ "TLS_ECDH_anon_WITH_NULL_SHA:SSL_RSA_WITH_NULL_MD5:SSL_RSA_WITH_DES_CBC_SHA:SSL_DHE_RSA_WITH_DES_CBC_SHA:SSL_DHE_DSS_WITH_DES_CBC_SHA:"
+ "SSL_DH_anon_WITH_DES_CBC_SHA:SSL_RSA_EXPORT_WITH_RC4_40_MD5:SSL_DH_anon_EXPORT_WITH_RC4_40_MD5:SSL_RSA_EXPORT_WITH_DES40_CBC_SHA:"
+ "SSL_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA:SSL_DHE_DSS_EXPORT_WITH_DES40_CBC_SHA:SSL_DH_anon_EXPORT_WITH_DES40_CBC_SHA:TLS_KRB5_WITH_RC4_128_SHA:"
+ "TLS_KRB5_WITH_RC4_128_MD5:TLS_KRB5_WITH_3DES_EDE_CBC_SHA:TLS_KRB5_WITH_3DES_EDE_CBC_MD5:TLS_KRB5_WITH_DES_CBC_SHA:TLS_KRB5_WITH_DES_CBC_MD5:"
+ "TLS_KRB5_EXPORT_WITH_RC4_40_SHA:TLS_KRB5_EXPORT_WITH_RC4_40_MD5:TLS_KRB5_EXPORT_WITH_DES_CBC_40_SHA:TLS_KRB5_EXPORT_WITH_DES_CBC_40_MD5";
//See Note 2.
private static final String jsseCiphersEnabledByDefault = "TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384:TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384:TLS_RSA_WITH_AES_256_CBC_SHA256:"
+ "TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384:TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384:TLS_DHE_RSA_WITH_AES_256_CBC_SHA256:"
+ "TLS_DHE_DSS_WITH_AES_256_CBC_SHA256:TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA:TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA:TLS_RSA_WITH_AES_256_CBC_SHA:"
+ "TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA:TLS_ECDH_RSA_WITH_AES_256_CBC_SHA:TLS_DHE_RSA_WITH_AES_256_CBC_SHA:TLS_DHE_DSS_WITH_AES_256_CBC_SHA:"
+ "TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256:TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256:TLS_RSA_WITH_AES_128_CBC_SHA256:TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256:"
+ "TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256:TLS_DHE_RSA_WITH_AES_128_CBC_SHA256:TLS_DHE_DSS_WITH_AES_128_CBC_SHA256:TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA:"
+ "TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA:TLS_RSA_WITH_AES_128_CBC_SHA:TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA:TLS_ECDH_RSA_WITH_AES_128_CBC_SHA:"
+ "TLS_DHE_RSA_WITH_AES_128_CBC_SHA:TLS_DHE_DSS_WITH_AES_128_CBC_SHA:TLS_ECDHE_ECDSA_WITH_RC4_128_SHA:TLS_ECDHE_RSA_WITH_RC4_128_SHA:"
+ "SSL_RSA_WITH_RC4_128_SHA:TLS_ECDH_ECDSA_WITH_RC4_128_SHA:TLS_ECDH_RSA_WITH_RC4_128_SHA:TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA:"
+ "TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA:SSL_RSA_WITH_3DES_EDE_CBC_SHA:TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA:TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA:"
+ "SSL_DHE_RSA_WITH_3DES_EDE_CBC_SHA:SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA:SSL_RSA_WITH_RC4_128_MD5:TLS_EMPTY_RENEGOTIATION_INFO_SCSV";
//A lot of them are not yet supported on jsse, See Note 1.
private static final String jsseCompleteCipherList = "SSL_DH_anon_EXPORT_WITH_DES40_CBC_SHA:SSL_DH_anon_EXPORT_WITH_RC4_40_MD5:SSL_DH_anon_WITH_3DES_EDE_CBC_SHA:"
+ "TLS_DH_anon_WITH_AES_128_CBC_SHA:TLS_DH_anon_WITH_AES_128_CBC_SHA256:TLS_DH_anon_WITH_AES_128_GCM_SHA256:TLS_DH_anon_WITH_AES_256_CBC_SHA:"
+ "TLS_DH_anon_WITH_AES_256_CBC_SHA256:TLS_DH_anon_WITH_AES_256_GCM_SHA384:TLS_DH_anon_WITH_CAMELLIA_128_CBC_SHA:TLS_DH_anon_WITH_CAMELLIA_128_CBC_SHA256:"
+ "TLS_DH_anon_WITH_CAMELLIA_256_CBC_SHA:TLS_DH_anon_WITH_CAMELLIA_256_CBC_SHA256:SSL_DH_anon_WITH_DES_CBC_SHA:SSL_DH_anon_WITH_RC4_128_MD5:"
+ "TLS_DH_anon_WITH_SEED_CBC_SHA:SSL_DH_DSS_EXPORT_WITH_DES40_CBC_SHA:SSL_DH_DSS_WITH_3DES_EDE_CBC_SHA:TLS_DH_DSS_WITH_AES_128_CBC_SHA:"
+ "TLS_DH_DSS_WITH_AES_128_CBC_SHA256:TLS_DH_DSS_WITH_AES_128_GCM_SHA256:TLS_DH_DSS_WITH_AES_256_CBC_SHA:TLS_DH_DSS_WITH_AES_256_CBC_SHA256:"
+ "TLS_DH_DSS_WITH_AES_256_GCM_SHA384:TLS_DH_DSS_WITH_CAMELLIA_128_CBC_SHA:TLS_DH_DSS_WITH_CAMELLIA_128_CBC_SHA256:TLS_DH_DSS_WITH_CAMELLIA_256_CBC_SHA:"
+ "TLS_DH_DSS_WITH_CAMELLIA_256_CBC_SHA256:SSL_DH_DSS_WITH_DES_CBC_SHA:TLS_DH_DSS_WITH_SEED_CBC_SHA:SSL_DH_RSA_EXPORT_WITH_DES40_CBC_SHA:"
+ "SSL_DH_RSA_WITH_3DES_EDE_CBC_SHA:TLS_DH_RSA_WITH_AES_128_CBC_SHA:TLS_DH_RSA_WITH_AES_128_CBC_SHA256:TLS_DH_RSA_WITH_AES_128_GCM_SHA256:"
+ "TLS_DH_RSA_WITH_AES_256_CBC_SHA:TLS_DH_RSA_WITH_AES_256_CBC_SHA256:TLS_DH_RSA_WITH_AES_256_GCM_SHA384:TLS_DH_RSA_WITH_CAMELLIA_128_CBC_SHA:"
+ "TLS_DH_RSA_WITH_CAMELLIA_128_CBC_SHA256:TLS_DH_RSA_WITH_CAMELLIA_256_CBC_SHA:TLS_DH_RSA_WITH_CAMELLIA_256_CBC_SHA256:SSL_DH_RSA_WITH_DES_CBC_SHA:"
+ "TLS_DH_RSA_WITH_SEED_CBC_SHA:SSL_DHE_DSS_EXPORT_WITH_DES40_CBC_SHA:SSL_DHE_DSS_EXPORT1024_WITH_DES_CBC_SHA:SSL_DHE_DSS_EXPORT1024_WITH_RC4_56_SHA:"
+ "SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA:TLS_DHE_DSS_WITH_AES_128_CBC_SHA:TLS_DHE_DSS_WITH_AES_128_CBC_SHA256:TLS_DHE_DSS_WITH_AES_128_GCM_SHA256:"
+ "TLS_DHE_DSS_WITH_AES_256_CBC_SHA:TLS_DHE_DSS_WITH_AES_256_CBC_SHA256:TLS_DHE_DSS_WITH_AES_256_GCM_SHA384:TLS_DHE_DSS_WITH_CAMELLIA_128_CBC_SHA:"
+ "TLS_DHE_DSS_WITH_CAMELLIA_128_CBC_SHA256:TLS_DHE_DSS_WITH_CAMELLIA_256_CBC_SHA:TLS_DHE_DSS_WITH_CAMELLIA_256_CBC_SHA256:SSL_DHE_DSS_WITH_DES_CBC_SHA:"
+ "SSL_DHE_DSS_WITH_RC4_128_SHA:TLS_DHE_DSS_WITH_SEED_CBC_SHA:TLS_DHE_PSK_WITH_3DES_EDE_CBC_SHA:TLS_DHE_PSK_WITH_AES_128_CBC_SHA:"
+ "TLS_DHE_PSK_WITH_AES_128_CBC_SHA256:TLS_DHE_PSK_WITH_AES_128_GCM_SHA256:TLS_DHE_PSK_WITH_AES_256_CBC_SHA:TLS_DHE_PSK_WITH_AES_256_CBC_SHA384:"
+ "TLS_DHE_PSK_WITH_AES_256_GCM_SHA384:TLS_DHE_PSK_WITH_NULL_SHA:TLS_DHE_PSK_WITH_NULL_SHA256:TLS_DHE_PSK_WITH_NULL_SHA384:"
+ "TLS_DHE_PSK_WITH_RC4_128_SHA:SSL_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA:SSL_DHE_RSA_WITH_3DES_EDE_CBC_SHA:TLS_DHE_RSA_WITH_AES_128_CBC_SHA:"
+ "TLS_DHE_RSA_WITH_AES_128_CBC_SHA256:TLS_DHE_RSA_WITH_AES_128_GCM_SHA256:TLS_DHE_RSA_WITH_AES_256_CBC_SHA:TLS_DHE_RSA_WITH_AES_256_CBC_SHA256:"
+ "TLS_DHE_RSA_WITH_AES_256_GCM_SHA384:TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA:TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA256:TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA:"
+ "TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA256:SSL_DHE_RSA_WITH_DES_CBC_SHA:TLS_DHE_RSA_WITH_SEED_CBC_SHA:TLS_ECDH_anon_WITH_3DES_EDE_CBC_SHA:"
+ "TLS_ECDH_anon_WITH_AES_128_CBC_SHA:TLS_ECDH_anon_WITH_AES_256_CBC_SHA:TLS_ECDH_anon_WITH_NULL_SHA:TLS_ECDH_anon_WITH_RC4_128_SHA:"
+ "TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA:TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA:TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256:TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256:"
+ "TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA:TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384:TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384:TLS_ECDH_ECDSA_WITH_NULL_SHA:"
+ "TLS_ECDH_ECDSA_WITH_RC4_128_SHA:TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA:TLS_ECDH_RSA_WITH_AES_128_CBC_SHA:TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256:"
+ "TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256:TLS_ECDH_RSA_WITH_AES_256_CBC_SHA:TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384:TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384:"
+ "TLS_ECDH_RSA_WITH_NULL_SHA:TLS_ECDH_RSA_WITH_RC4_128_SHA:TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA:TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA:"
+ "TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256:TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256:TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA:"
+ "TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384:TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384:TLS_ECDHE_ECDSA_WITH_NULL_SHA:TLS_ECDHE_ECDSA_WITH_RC4_128_SHA:"
+ "TLS_ECDHE_PSK_WITH_3DES_EDE_CBC_SHA:TLS_ECDHE_PSK_WITH_AES_128_CBC_SHA:TLS_ECDHE_PSK_WITH_AES_128_CBC_SHA256:TLS_ECDHE_PSK_WITH_AES_256_CBC_SHA:"
+ "TLS_ECDHE_PSK_WITH_AES_256_CBC_SHA384:TLS_ECDHE_PSK_WITH_NULL_SHA:TLS_ECDHE_PSK_WITH_NULL_SHA256:TLS_ECDHE_PSK_WITH_NULL_SHA384:"
+ "TLS_ECDHE_PSK_WITH_RC4_128_SHA:TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA:TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA:TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256:"
+ "TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256:TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA:TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384:TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384:"
+ "TLS_ECDHE_RSA_WITH_NULL_SHA:TLS_ECDHE_RSA_WITH_RC4_128_SHA:TLS_EMPTY_RENEGOTIATION_INFO_SCSV:SSL_FORTEZZA_DMS_WITH_FORTEZZA_CBC_SHA:"
+ "SSL_FORTEZZA_DMS_WITH_NULL_SHA:TLS_KRB5_EXPORT_WITH_DES_CBC_40_MD5:TLS_KRB5_EXPORT_WITH_DES_CBC_40_SHA:TLS_KRB5_EXPORT_WITH_RC2_CBC_40_MD5:"
+ "TLS_KRB5_EXPORT_WITH_RC2_CBC_40_SHA:TLS_KRB5_EXPORT_WITH_RC4_40_MD5:TLS_KRB5_EXPORT_WITH_RC4_40_SHA:TLS_KRB5_WITH_3DES_EDE_CBC_MD5:"
+ "TLS_KRB5_WITH_3DES_EDE_CBC_SHA:TLS_KRB5_WITH_DES_CBC_MD5:TLS_KRB5_WITH_DES_CBC_SHA:TLS_KRB5_WITH_IDEA_CBC_MD5:TLS_KRB5_WITH_IDEA_CBC_SHA:"
+ "TLS_KRB5_WITH_RC4_128_MD5:TLS_KRB5_WITH_RC4_128_SHA:TLS_PSK_WITH_3DES_EDE_CBC_SHA:TLS_PSK_WITH_AES_128_CBC_SHA:TLS_PSK_WITH_AES_128_CBC_SHA256:"
+ "TLS_PSK_WITH_AES_128_GCM_SHA256:TLS_PSK_WITH_AES_256_CBC_SHA:TLS_PSK_WITH_AES_256_CBC_SHA384:TLS_PSK_WITH_AES_256_GCM_SHA384:TLS_PSK_WITH_NULL_SHA:"
+ "TLS_PSK_WITH_NULL_SHA256:TLS_PSK_WITH_NULL_SHA384:TLS_PSK_WITH_RC4_128_SHA:SSL_RSA_EXPORT_WITH_DES40_CBC_SHA:SSL_RSA_EXPORT_WITH_RC2_CBC_40_MD5:"
+ "SSL_RSA_EXPORT_WITH_RC4_40_MD5:SSL_RSA_EXPORT1024_WITH_DES_CBC_SHA:SSL_RSA_EXPORT1024_WITH_RC4_56_SHA:SSL_RSA_FIPS_WITH_3DES_EDE_CBC_SHA:"
+ "SSL_RSA_FIPS_WITH_DES_CBC_SHA:TLS_RSA_PSK_WITH_3DES_EDE_CBC_SHA:TLS_RSA_PSK_WITH_AES_128_CBC_SHA:TLS_RSA_PSK_WITH_AES_128_CBC_SHA256:"
+ "TLS_RSA_PSK_WITH_AES_128_GCM_SHA256:TLS_RSA_PSK_WITH_AES_256_CBC_SHA:TLS_RSA_PSK_WITH_AES_256_CBC_SHA384:TLS_RSA_PSK_WITH_AES_256_GCM_SHA384:"
+ "TLS_RSA_PSK_WITH_NULL_SHA:TLS_RSA_PSK_WITH_NULL_SHA256:TLS_RSA_PSK_WITH_NULL_SHA384:TLS_RSA_PSK_WITH_RC4_128_SHA:SSL_RSA_WITH_3DES_EDE_CBC_SHA:"
+ "TLS_RSA_WITH_AES_128_CBC_SHA:TLS_RSA_WITH_AES_128_CBC_SHA256:TLS_RSA_WITH_AES_128_GCM_SHA256:TLS_RSA_WITH_AES_256_CBC_SHA:TLS_RSA_WITH_AES_256_CBC_SHA256:"
+ "TLS_RSA_WITH_AES_256_GCM_SHA384:TLS_RSA_WITH_CAMELLIA_128_CBC_SHA:TLS_RSA_WITH_CAMELLIA_128_CBC_SHA256:TLS_RSA_WITH_CAMELLIA_256_CBC_SHA:"
+ "TLS_RSA_WITH_CAMELLIA_256_CBC_SHA256:SSL_RSA_WITH_DES_CBC_SHA:SSL_RSA_WITH_IDEA_CBC_SHA:SSL_RSA_WITH_NULL_MD5:SSL_RSA_WITH_NULL_SHA:"
+ "TLS_RSA_WITH_NULL_SHA256:SSL_RSA_WITH_RC4_128_MD5:SSL_RSA_WITH_RC4_128_SHA:TLS_RSA_WITH_SEED_CBC_SHA:TLS_SRP_SHA_DSS_WITH_3DES_EDE_CBC_SHA:"
+ "TLS_SRP_SHA_DSS_WITH_AES_128_CBC_SHA:TLS_SRP_SHA_DSS_WITH_AES_256_CBC_SHA:TLS_SRP_SHA_RSA_WITH_3DES_EDE_CBC_SHA:TLS_SRP_SHA_RSA_WITH_AES_128_CBC_SHA:"
+ "TLS_SRP_SHA_RSA_WITH_AES_256_CBC_SHA:TLS_SRP_SHA_WITH_3DES_EDE_CBC_SHA:TLS_SRP_SHA_WITH_AES_128_CBC_SHA:TLS_SRP_SHA_WITH_AES_256_CBC_SHA";
public static void main(String[] args) throws Exception {
String ciphers = jsseCiphersEnabledByDefault + ":" + jsseCiphersDisabledByDefault;
System.out.println("Using Hostname : port = " + HOST + " : " + PORT_TARGET);
//test enabled and the ones that disabled by default
testSSL(HOST, PORT_TARGET, PROTO_SSLV3, ciphers);
testSSL(HOST, PORT_TARGET, PROTO_TLSV1, ciphers);
testSSL(HOST, PORT_TARGET, PROTO_TLSV11, ciphers);
testSSL(HOST, PORT_TARGET, PROTO_TLSV12, ciphers);
//test weak ciphers
/* testSSL(HOST, PORT_TARGET, PROTO_SSLV3, jsseCiphersDisabledByDefault);
testSSL(HOST, PORT_TARGET, PROTO_TLSV1, jsseCiphersDisabledByDefault);
testSSL(HOST, PORT_TARGET, PROTO_TLSV11, jsseCiphersDisabledByDefault);
testSSL(HOST, PORT_TARGET, PROTO_TLSV12, jsseCiphersDisabledByDefault);*/
}
private static void testSSL(String hostname, int port, String version, String cipherSuitesToTest) {
try {
System.out.println("-------------------------");
System.out.println("Protocol : " + version);
ArrayList success = new ArrayList();
ArrayList unsupported = new ArrayList();
ArrayList fail = new ArrayList();
SSLSocketFactory factory = (SSLSocketFactory) SSLSocketFactory
.getDefault();
SSLSocket socket = (SSLSocket) factory.createSocket(hostname, port);
//set the SSL version to be used
String[] prots = { version };
socket.setEnabledProtocols(prots);
String[] cipherSuitesClient = cipherSuitesToTest.split(":");
for (String ciphers : cipherSuitesClient) {
socket = (SSLSocket) factory.createSocket(hostname, port);
socket.setEnabledProtocols(prots);
String[] array = { ciphers };
//try making a handshake
try {
socket.setEnabledCipherSuites(array);
socket.startHandshake();
success.add(ciphers);
} catch (javax.net.ssl.SSLHandshakeException e) {
fail.add(ciphers);
} catch (java.lang.IllegalArgumentException e){
if (e.getMessage().contains("Unsupported ciphersuite") || e.getMessage().contains("Cannot support"))
unsupported.add(ciphers);
else
e.printStackTrace();
}
catch (Exception e) {
System.out.println(ciphers + ":" + e.getClass() + " "
+ e.getMessage());
}
socket.close();
}
System.out.println("Testing " + version + " ciphers. Count: "
+ cipherSuitesClient.length);
System.out.println("Successful Handshake count = "
+ success.size());
Collections.sort(success);
for (String name : success) {
System.out.println("[" + version + "]" + " +" + name);
}
System.out.println("Unsupported list. Count = " + unsupported.size());
Collections.sort(unsupported);
if(VERBOSE){
for (String name : unsupported) {
System.out.println("[" + version + "]" + "XXX " + name);
}
}
System.out.println("Handshake Failed Count = " + fail.size());
if(VERBOSE){
for (String name : fail) {
System.out.println("[" + version + "]" + "-" + name);
}
}
} catch (Exception e) {
e.printStackTrace();
}
}
}