My last post came almost about 10 years back. I loved this little space that I created for myself. After 10 years, I feel I can channel out my inner thoughts. A lot of hard work went into that. And a certain sense of finding oneself. I was a seeker, I am a seeker and I will be a seeker for centuries to come.
Reverse Shell
Free spirit as in Freedom.
Monday, February 26, 2024
Tuesday, December 2, 2014
Can't locate Config/IniFiles.pm in @INC - SSLAudit
SSLAudit needs a few modules to be installed.
aditya@ubuntu:~$ perl SSLAudit.pl
Can't locate Config/IniFiles.pm in @INC (you may need to install the Config::IniFiles module) (@INC contains: /etc/perl /usr/local/lib/perl/5.18.2 /usr/local/share/perl/5.18.2 /usr/lib/perl5 /usr/share/perl5 /usr/lib/perl/5.18 /usr/share/perl/5.18 /usr/local/lib/site_perl .) at SSLAudit.pl line 9.
BEGIN failed--compilation aborted at SSLAudit.pl line 9.
aditya@ubuntu:~$ sudo cpan install Config::IniFiles
=========
aditya@ubuntu:~$ perl SSLAudit.pl
Can't locate Time/ParseDate.pm in @INC (you may need to install the Time::ParseDate module) (@INC contains: /etc/perl /usr/local/lib/perl/5.18.2 /usr/local/share/perl/5.18.2 /usr/lib/perl5 /usr/share/perl5 /usr/lib/perl/5.18 /usr/share/perl/5.18 /usr/local/lib/site_perl .) at SSLAudit.pl line 13.
BEGIN failed--compilation aborted at SSLAudit.pl line 13.
===========
aditya@ubuntu:~$ sudo cpan install Time::ParseDate
===========
aditya@ubuntu:~$ perl SSLAudit.pl
Can't locate Config/IniFiles.pm in @INC (you may need to install the Config::IniFiles module) (@INC contains: /etc/perl /usr/local/lib/perl/5.18.2 /usr/local/share/perl/5.18.2 /usr/lib/perl5 /usr/share/perl5 /usr/lib/perl/5.18 /usr/share/perl/5.18 /usr/local/lib/site_perl .) at SSLAudit.pl line 9.
BEGIN failed--compilation aborted at SSLAudit.pl line 9.
aditya@ubuntu:~$ sudo cpan install Config::IniFiles
=========
aditya@ubuntu:~$ perl SSLAudit.pl
Can't locate Time/ParseDate.pm in @INC (you may need to install the Time::ParseDate module) (@INC contains: /etc/perl /usr/local/lib/perl/5.18.2 /usr/local/share/perl/5.18.2 /usr/lib/perl5 /usr/share/perl5 /usr/lib/perl/5.18 /usr/share/perl/5.18 /usr/local/lib/site_perl .) at SSLAudit.pl line 13.
BEGIN failed--compilation aborted at SSLAudit.pl line 13.
===========
aditya@ubuntu:~$ sudo cpan install Time::ParseDate
===========
Friday, November 28, 2014
CVE-2014-2309 - ICMPv6 Router Advertisement flood Denial of service
CVE reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2309
I guess it works only if your Linux box accepts IPV6 router advertisement packets. Do you want to check if your Linux accepts router advertisement packets?
Check the kernel settings for IPV6:
http://www.tldp.org/HOWTO/Linux+IPv6-HOWTO/proc-sys-net-ipv6..html
Check in /proc/sys/net/ipv6/conf//accept_ra setting, if 0 means disabled, if 1 means setting is enabled.
I guess it works only if your Linux box accepts IPV6 router advertisement packets. Do you want to check if your Linux accepts router advertisement packets?
Check the kernel settings for IPV6:
http://www.tldp.org/HOWTO/Linux+IPv6-HOWTO/proc-sys-net-ipv6..html
Check in /proc/sys/net/ipv6/conf/
Tuesday, October 28, 2014
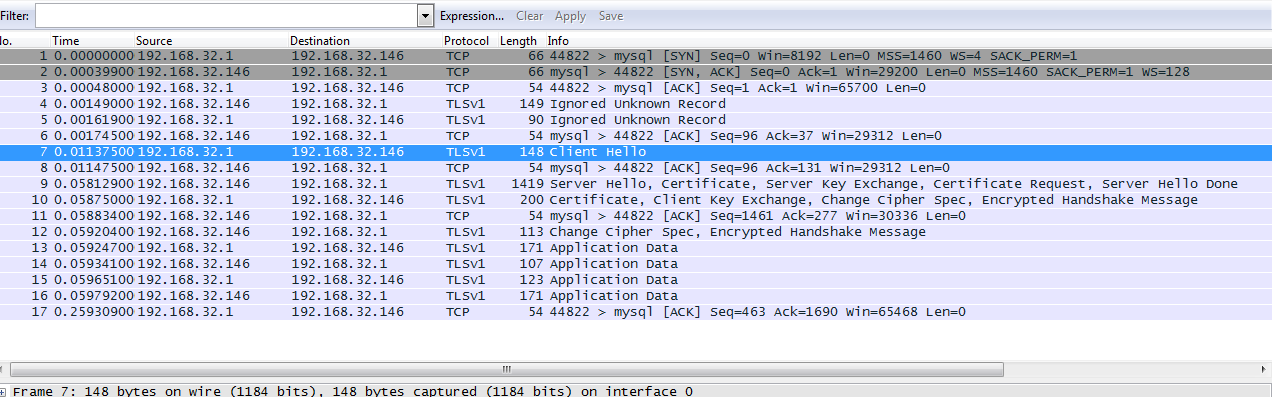
Mysql TLSv1 capture using Wireshark
I installed mysql and enabled SSL on it. And I was just wondering how to see if the encryption is really working. I dont know what SSL protocol mysql uses for encryption.
So I started wireshark and captured login using a remote machine.
The default capture will show you the protocol as mysql,
but inorder to see the SSL/TLS you need to decode the packets as SSL. The SSL handshake does not occur first, but is followed after a few mysql packet exchanges.
So I started wireshark and captured login using a remote machine.
The default capture will show you the protocol as mysql,
but inorder to see the SSL/TLS you need to decode the packets as SSL. The SSL handshake does not occur first, but is followed after a few mysql packet exchanges.
[Ubuntu 14.04] mysql with SSL: ERROR 2026 (HY000): SSL connection error: protocol version mismatch
I was trying to enable SSL on mysql in Ubuntu 14.04 and it was not easy.
1. Install simply, apt-get install mysql-client mysql-server and set a strong root password.
2. Generate openssl certs and enable SSL configurations in /etc/mysql/my.cnf like this:
#For the client: (localhost only)
[client]
port = 3306
socket = /var/run/mysqld/mysqld.sock
ssl=1
ssl-ca = /etc/mysql/ca-cert.pem
....
ssl=1ssl-ca=/etc/mysql/ca-cert.pem
ssl-cert=/etc/mysql/server-cert.pem
ssl-key=/etc/mysql/server-key.pem
ssl-cipher=DHE-RSA-AES256-SHA
Restart mysql, thats it. But while trying to connect (mysql -u root -p), I faced an error:
ERROR 2026 (HY000): SSL connection error: protocol version mismatch
Later I figured out, it was due to Bad certificates (well kind of..),
So generate the certificates using the commands here:
http://askubuntu.com/questions/194074/enabling-ssl-in-mysql
Once you connect, you can /s to confirm that your cipher is on:
--------------------------------------------------------------------------------------------
mysql -u root -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 36
Server version: 5.5.38-0ubuntu0.14.04.1 (Ubuntu)
Copyright (c) 2000, 2014, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> \s
--------------
mysql Ver 14.14 Distrib 5.5.38, for debian-linux-gnu (i686) using readline 6.3
Connection id: 36
Current database:
Current user: root@localhost
SSL: Cipher in use is DHE-RSA-AES256-SHA
Current pager: stdout
Using outfile: ''
Using delimiter: ;
Server version: 5.5.38-0ubuntu0.14.04.1 (Ubuntu)
Protocol version: 10
Connection: Localhost via UNIX socket
Server characterset: latin1
Db characterset: latin1
Client characterset: utf8
Conn. characterset: utf8
UNIX socket: /var/run/mysqld/mysqld.sock
Uptime: 11 days 1 hour 4 min 49 sec
Threads: 1 Questions: 109 Slow queries: 0 Opens: 171 Flush tables: 1 Open tables: 41 Queries per second avg: 0.000
--------------
mysql>
Now if you want to see mysql SSL in action using wireshark,
http://rhosted.blogspot.in/2014/10/mysql-tlsv1-capture-using-wireshark.html
More references:
http://askubuntu.com/questions/194074/enabling-ssl-in-mysql
Saturday, October 18, 2014
Eclipse plugin list
1. Python development
pydev - Python development on eclipse.
http://pydev.org/
2. Shell script development
http://sourceforge.net/projects/shelled/
Yeah, I know what you have been thinking. IDE for shell scripts, vi or the Linux editors are the best thing to write a shell script. However, if you want to keep a project like structure for shell scripts for reference and to show or explain the shell script to anyone, this eclipse editor comes in handy. Not a replacement for vi though. Another limitation for windows users is that you do not have anything to run and test the shell script if you are on windows.
3. Linux tools for eclipse
http://www.eclipse.org/linuxtools/
This works pretty well with Shelled, when you are on windows but you want to refer to the man pages in Linux. That was the only use I could find in windows.
4. Remote Systems Explorer
Although using eclipse to access remote file systems through SSH/telnet/RDP sounds crazy but this is very handy while working with shell scripts using the shell script editor shelled. You can readily scp the files to your test machine and execute the scripts right from the eclipse console.
You can find it on the eclipse market place.
http://marketplace.eclipse.org/content/remote-system-explorer-ssh-telnet-ftp-and-dstore-protocols#.VBBalPmSysw
5. JADclipse
The Java decompiler -
http://sourceforge.net/projects/jadclipse/
6. Eclipse color themes
http://eclipsecolorthemes.org/?view=plugin
wombat:
7. Maven eclipse plugin, m2eclipse
https://www.eclipse.org/m2e/
8. StartExplorer: Starts an explorer or a command prompt at the location of the file in eclipse.
http://marketplace.eclipse.org/node/641101#.VBEnufmSyig
9. Browsing databases (Oracle, mysql and postgresql) using Toad Extension:
http://marketplace.eclipse.org/content/toad-extension-eclipse#.VBE68PmSyig
pydev - Python development on eclipse.
http://pydev.org/
2. Shell script development
http://sourceforge.net/projects/shelled/
Yeah, I know what you have been thinking. IDE for shell scripts, vi or the Linux editors are the best thing to write a shell script. However, if you want to keep a project like structure for shell scripts for reference and to show or explain the shell script to anyone, this eclipse editor comes in handy. Not a replacement for vi though. Another limitation for windows users is that you do not have anything to run and test the shell script if you are on windows.
3. Linux tools for eclipse
http://www.eclipse.org/linuxtools/
This works pretty well with Shelled, when you are on windows but you want to refer to the man pages in Linux. That was the only use I could find in windows.
4. Remote Systems Explorer
Although using eclipse to access remote file systems through SSH/telnet/RDP sounds crazy but this is very handy while working with shell scripts using the shell script editor shelled. You can readily scp the files to your test machine and execute the scripts right from the eclipse console.
You can find it on the eclipse market place.
http://marketplace.eclipse.org/content/remote-system-explorer-ssh-telnet-ftp-and-dstore-protocols#.VBBalPmSysw
5. JADclipse
The Java decompiler -
http://sourceforge.net/projects/jadclipse/
6. Eclipse color themes
http://eclipsecolorthemes.org/?view=plugin
wombat:
7. Maven eclipse plugin, m2eclipse
https://www.eclipse.org/m2e/
8. StartExplorer: Starts an explorer or a command prompt at the location of the file in eclipse.
http://marketplace.eclipse.org/node/641101#.VBEnufmSyig
9. Browsing databases (Oracle, mysql and postgresql) using Toad Extension:
http://marketplace.eclipse.org/content/toad-extension-eclipse#.VBE68PmSyig
Monday, September 29, 2014
Shellshock: Patching GNU bash from source
Bash compilation notes, if you want to compile bash yourself. If you have an older version of bash and do not want to wait for your vendor, and you do not want to upgrade to the most latest version like 4.3. The patches for shellshock or CVE-2014-6271 are available for all the bash versions. However, early fixes have not been stable and the attack vectors are still evolving, so we still need to keep an eye on the developments.
Check what version you have by:
bash --version
Let's say I am running an old version of bash v 3.00
Before patching, I see that the trailing code after the function definition is getting executed:
Step 1: Download the bash source (base version) from:
http://ftp.gnu.org/gnu/bash/
Step 2: Get all the patches for bash 3.0 from the patches location and save them in a directory say patches:
mkdir patches
http://ftp.gnu.org/gnu/bash/bash-3.0-patches/
Save them as bash30-001.patch etc, i.e. with a patch extension for easy handling.
Step 3: Extract bash and copy patches to the src dir:
Step 5: Confirm that it got applied, second last line says 19:
Step 6: Compile bash:
I am not sure if this test is complete, as there are other ways to exploit it as well. I saw some of them here:
http://stevejenkins.com/blog/2014/09/how-to-manually-update-bash-to-patch-shellshock-bug-on-older-fedora-based-systems/
Nevertheless, there have been 3 bash patches so far, and I have applied all of them.
Extras:
If you just want the compiled package and want to install it on different machines, then just use --prefix=destination_directory, like:
tarball it, so that you can distribute it to different machines:
mv /bin/bash /bin/bash_old
Extraction:
References:
http://apple.stackexchange.com/questions/146849/how-do-i-recompile-bash-to-avoid-shellshock-the-remote-exploit-cve-2014-6271-an
http://stevejenkins.com/blog/2014/09/how-to-manually-update-bash-to-patch-shellshock-bug-on-older-fedora-based-systems/
Check what version you have by:
bash --version
Let's say I am running an old version of bash v 3.00
Before patching, I see that the trailing code after the function definition is getting executed:
[test@test ~]# env x='() { :;}; echo vulnerable' bash -c 'echo hello'
vulnerable
hello
Step 1: Download the bash source (base version) from:
http://ftp.gnu.org/gnu/bash/
wget http://ftp.gnu.org/gnu/bash/bash-3.0.tar.gz
Step 2: Get all the patches for bash 3.0 from the patches location and save them in a directory say patches:
mkdir patches
http://ftp.gnu.org/gnu/bash/bash-3.0-patches/
Save them as bash30-001.patch etc, i.e. with a patch extension for easy handling.
[test@test patches]# ls
bash30-001.patch bash30-005.patch bash30-009.patch bash30-013.patch bash30-017.patch
bash30-002.patch bash30-006.patch bash30-010.patch bash30-014.patch bash30-018.patch
bash30-003.patch bash30-007.patch bash30-011.patch bash30-015.patch bash30-019.patch
bash30-004.patch bash30-008.patch bash30-012.patch bash30-016.patch
Step 3: Extract bash and copy patches to the src dir:
Copy the patches to the extracted bash source directory:
[test@test bash_test]# tar -xvzf bash-3.0.tar.gz
Step 4: Apply the patches:
[test@test bash-3.0]# cp ../patches/*.patch .
[test@test bash-3.0]# for x in *.patch; do patch -p0 < $x; done
Step 5: Confirm that it got applied, second last line says 19:
[root@cap bash-3.0]# cat patchlevel.h
...
#define PATCHLEVEL 19
#endif /* _PATCHLEVEL_H_ */
Step 6: Compile bash:
Step 7: After patching, test:
./configure ; make ; make install
The statement echo vulnerable, did not execute.
[test@test bash-3.0]# env x='() { :;}; echo vulnerable' bash -c 'echo hello'
hello
I am not sure if this test is complete, as there are other ways to exploit it as well. I saw some of them here:
http://stevejenkins.com/blog/2014/09/how-to-manually-update-bash-to-patch-shellshock-bug-on-older-fedora-based-systems/
Nevertheless, there have been 3 bash patches so far, and I have applied all of them.
Extras:
If you just want the compiled package and want to install it on different machines, then just use --prefix=destination_directory, like:
This generates 4 directories (bin, info, man and share)
./configure --prefix=/home/test/compiled; make ; make install
tarball it, so that you can distribute it to different machines:
Before you extract the files in your root directory, make a backup of old bash binary in /bin/bash.
cd /home/test/compiled
tar -cvzf bash_3.0.19_patched_binary.tar.gz bin/ info/ man/ share/
mv /bin/bash /bin/bash_old
Extraction:
tar -xvzf bash_3.0.19_patched_binary.tar.gz -C /
References:
http://apple.stackexchange.com/questions/146849/how-do-i-recompile-bash-to-avoid-shellshock-the-remote-exploit-cve-2014-6271-an
http://stevejenkins.com/blog/2014/09/how-to-manually-update-bash-to-patch-shellshock-bug-on-older-fedora-based-systems/
Subscribe to:
Posts (Atom)